Challenges in Federal Agencies Protecting Classified Information
by Rafay Muneer on Nov 21, 2024 2:40:03 AM

Think about your agency’s classified information—sensitive government data, military secrets, or intelligence reports getting exposed due to a preventable security lapse.
Safeguarding classified information is crucial because a breach like this could damage national security and lead to millions of dollars in recovery costs.
Devastating, isn’t it?
Yet, federal agencies are constantly walking on a tightrope, balancing between the need for robust security measures and the growing complexity of today’s digital threats. The challenges in safeguarding classified information are multifaceted and daunting, affecting every corner of an organization, from the CISO down to the IT support teams.
Now that we are aware of the problem at hand, let’s break it down: what’s causing these vulnerabilities, why do they persist, and how can your agency overcome them?
The Complex Landscape of Federal Data Security
When it comes to safeguarding classified information, the stakes are higher than ever. Federal agencies are tasked with protecting some of the most sensitive data in the world, from military strategies to confidential citizen information. The increasing digitization of information combined with advanced cybersecurity threats makes it more challenging to keep classified information secure. Here are some of the most pressing issues:
Aging IT Infrastructure
Many federal agencies rely on legacy IT systems that were built decades ago. These systems often don’t have the advanced security features required to safeguard today’s classified information. The outdated technology cannot easily integrate with modern cybersecurity solutions, making it vulnerable to cyberattacks.
Moreover, maintaining these old systems consumes a significant portion of IT budgets. In 2016, it was reported that the US government spent a large portion of its $80 million technology budget to maintain outdated hardware. This leaves little room for investment in new, more secure technologies. The result? An open invitation for hackers and foreign adversaries looking for a way in.
Inconsistent Compliance with Federal Regulations
Federal agencies must comply with strict regulations, such as the Federal Information Security Management Act (FISMA), the National Institute of Standards and Technology (NIST) guidelines, and others. However, maintaining compliance is a moving target. Regulations change, new threats emerge, and many agencies struggle to keep up.
Compliance isn't just about ticking boxes; it’s about ensuring that every aspect of data security—from encryption to access controls—meets the required standards. Agencies that fail to comply not only risk data breaches but also face legal penalties, which can cripple operations.
Human Error and Insider Threats
Even with the best cybersecurity measures in place, human error remains a leading cause of data breaches. Whether it’s a staff member accidentally sending classified information to the wrong email address or failing to properly secure a physical file, mistakes happen. In federal agencies, these mistakes can be catastrophic.
Worse yet, insider threats—whether from disgruntled employees or those with malicious intent—pose a unique challenge. These individuals often have access to sensitive data and are familiar with the security protocols in place, making them harder to detect.
Advanced Persistent Threats (APTs) and Nation-State Attacks
Federal agencies are prime targets for Advanced Persistent Threats (APTs), which are often sponsored by foreign governments. APTs are highly sophisticated cyberattacks that infiltrate networks and remain undetected for extended periods, gathering classified information or disrupting operations.
These nation-state attacks often involve cutting-edge techniques, including zero-day exploits, spear phishing, and ransomware, all aimed at accessing classified data or crippling federal operations. The complexity of these attacks makes them difficult to defend against, even for well-resourced agencies.
Data Volume and Complexity
The volume of classified information being generated today is staggering. From intelligence agencies gathering real-time data to government research organizations managing sensitive projects, the amount of data that needs protection is growing exponentially.
With this increased data comes increased complexity. Data is being stored across multiple platforms, both on-premises and in the cloud. Securing it requires an approach that considers the entire data lifecycle—from creation to storage to eventual destruction. Unfortunately, many agencies lack the resources or expertise to effectively manage and secure this vast amount of information.
Why These Challenges Are a Ticking Time Bomb
The problems outlined above aren’t just theoretical—they’re real, and they’re affecting federal agencies every day. But what makes these challenges so difficult to solve? Let’s dig deeper into the pain points.
Legacy Systems: A Hacker’s Paradise
The older the system, the more vulnerable it is. Most legacy systems were never designed with cybersecurity in mind. They don’t have the ability to support modern encryption protocols or multi-factor authentication, leaving classified data wide open to attacks. Hackers are well aware of these vulnerabilities and are constantly probing for weak spots.
What’s worse is that upgrading these systems isn’t just a matter of flipping a switch. It requires a massive financial investment, not to mention the time and resources needed to migrate sensitive data without disrupting daily operations.
Compliance Fatigue
Regulations like FISMA and NIST are incredibly detailed, and staying compliant can feel like chasing a moving target. Agencies often dedicate entire teams just to managing compliance, and even then, things slip through the cracks. One missed update, one unpatched vulnerability, and your agency could be facing not just a data breach but also a costly audit.
Compliance fatigue is real. The sheer volume of regulations and the evolving nature of threats make it difficult for even the most well-prepared agencies to stay ahead.
The Invisible Insider Threat
What makes insider threats so terrifying is their invisibility. They don’t need to hack into your systems—they already have access. Detecting insider threats requires advanced monitoring and analytics, but most federal agencies don’t have these capabilities in place.
And then there’s the human error factor. People make mistakes, and those mistakes can lead to classified information being exposed. Training programs help, but they’re not foolproof. The more classified information an agency manages, the more opportunities there are for human error.
The Evolving Nature of Cyberattacks
Cyberattacks aren’t just getting more frequent; they’re getting more sophisticated. APTs can stay hidden in your system for months or even years, quietly siphoning off classified data or planting backdoors for future access. By the time you detect them, it’s often too late.
Nation-state actors are constantly developing new tools and techniques to breach federal systems. With unlimited resources at their disposal, they can launch highly targeted, persistent attacks that are incredibly difficult to defend against.
Overwhelmed by Data
The sheer volume of classified data being generated is overwhelming. Securing it all—across multiple platforms and environments—requires significant resources. Unfortunately, many agencies are understaffed and underfunded, leaving critical gaps in their data security strategies.
Managing this data also requires visibility. If you don’t know where your classified information is stored, how it’s being accessed, or who has access to it, you can’t secure it. This lack of visibility is one of the biggest challenges federal agencies faces.
How Federal Agencies Can Safeguard Classified Information
Now that we’ve examined the challenges let’s talk about how federal agencies can overcome them. The solution isn’t a one-size-fits-all approach, but a combination of technology, policy, and best practices tailored to each agency’s unique needs.
-
Modernize IT Infrastructure
Upgrading legacy systems is essential to securing classified information. While this may seem like a daunting task, the benefits far outweigh the costs. Modern systems come equipped with advanced security features like encryption, access controls, and multi-factor authentication, all of which are critical for protecting sensitive data.
Consider transitioning to cloud solutions that meet federal security standards. Many cloud providers offer FedRAMP-authorized services, which provide the necessary security controls for handling classified information.
-
Streamline Compliance Processes
Compliance doesn’t have to be a burden. By automating compliance management, agencies can reduce the time and resources spent on manual processes. Solutions that offer real-time monitoring and reporting can help agencies stay compliant with FISMA, NIST, and other regulations without the need for constant oversight.
Another key strategy is to adopt a risk-based approach to compliance. Focus on the areas that pose the greatest risk to your agency and prioritize those in your compliance efforts. This will help ensure that you’re not just ticking boxes but actively improving your security posture.
-
Enhance Insider Threat Detection
Detecting insider threats requires more than just monitoring user activity. Advanced analytics and AI-driven tools can help identify abnormal behavior patterns that may indicate an insider threat. These tools can alert security teams to potential risks before they escalate into full-blown breaches.
Training employees on the importance of data security is also critical. Regular training sessions, combined with strict access controls, can help minimize the risk of human error leading to a security incident.
-
Defend Against Advanced Persistent Threats (APTs)
Fighting APTs requires a multi-layered defense strategy. This includes endpoint protection, network monitoring, and incident response plans that are designed to detect and respond to APTs quickly. Implementing solutions that can automatically quarantine suspicious activity can help prevent APTs from gaining a foothold in your system.
Regular penetration testing and red teaming exercises can also help identify potential vulnerabilities before attackers do. By simulating an APT attack, you can test your defenses and make necessary improvements to your security posture.
-
Improve Data Management and Visibility
Data management is key to safeguarding classified information. Agencies need to know where their classified data is stored, who has access to it, and how it’s being used. This requires robust data governance policies and tools that provide visibility into data activity across all platforms.
Consider implementing a data loss prevention (DLP) solution that monitors and controls the movement of sensitive data. This can help prevent unauthorized access or transfer of classified information.1
-
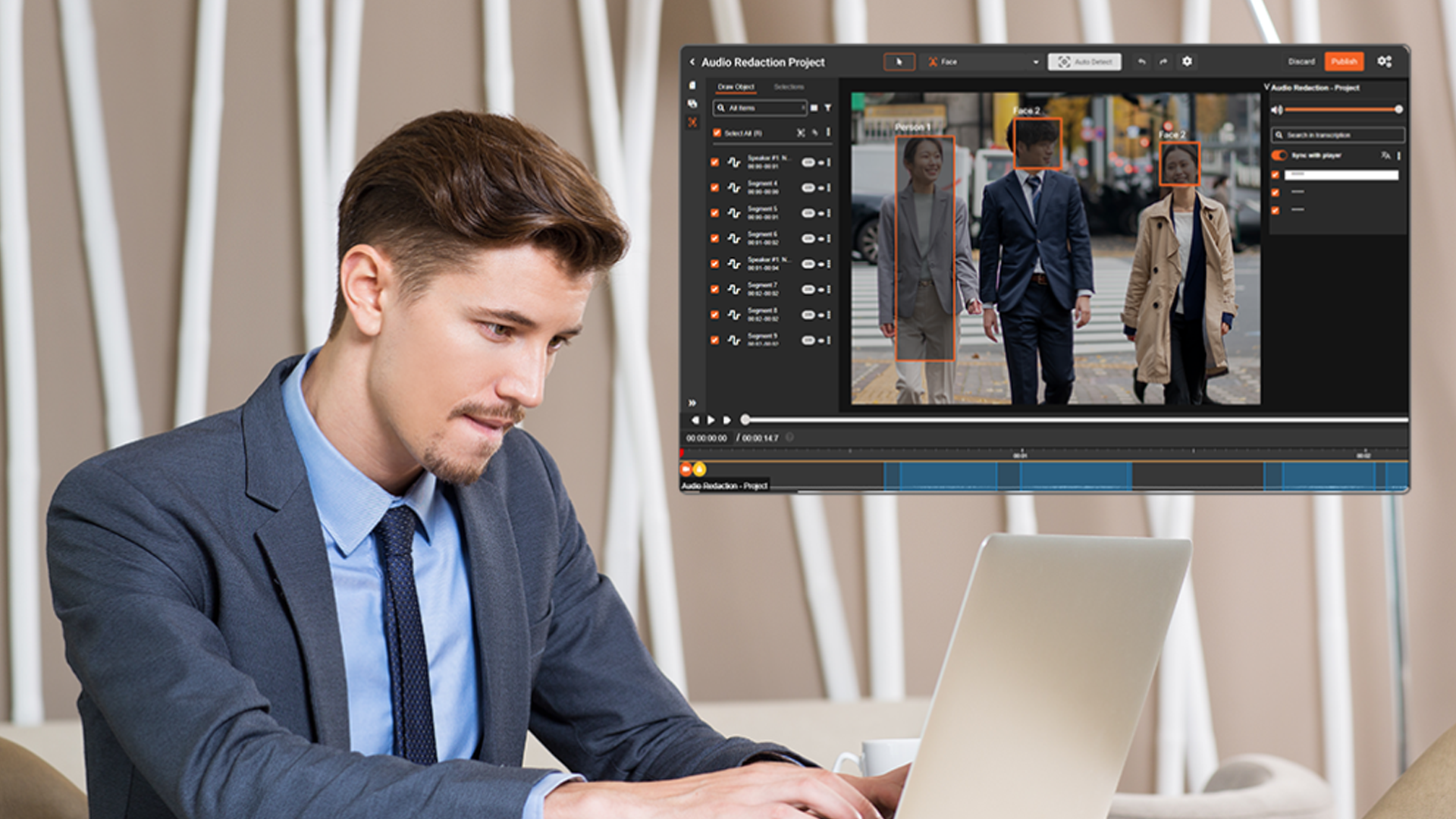
Implement Effective Redaction Practices
Redaction is a crucial step in protecting classified information, especially when sharing documents with stakeholders who may not have the necessary security clearance. Proper redaction ensures that sensitive data is effectively obscured, minimizing the risk of unintentional disclosure.
Agencies should implement standardized redaction policies that outline when and how to redact information. Automated redaction tools can help streamline this process, ensuring that sensitive content is consistently and thoroughly removed before documents are shared. This not only protects classified information but also enhances compliance with federal regulations regarding data sharing.
Furthermore, training staff on redaction best practices is essential. Employees must understand the importance of redacting sensitive information, as well as the potential consequences of failing to do so. By prioritizing effective redaction, federal agencies can significantly reduce the risk of classified information falling into the wrong hands.
Building a Secure Future for Federal Agencies
The protection of classified information is paramount to national security. Federal agencies operate in a dynamic threat landscape, facing a constant barrage of sophisticated cyberattacks and evolving vulnerabilities. To safeguard sensitive data and maintain operational integrity, a comprehensive and proactive approach is essential.
Ultimately, the goal is not merely to prevent breaches but to build a resilient and secure future for federal agencies. This requires a sustained commitment to innovation, collaboration, and a risk-based approach to cybersecurity. By prioritizing these measures, agencies can protect their critical assets, maintain public trust, and ensure the continued effectiveness of national security operations.
People Also Ask
What are the main regulations federal agencies must follow to safeguard classified information?
Federal agencies must comply with several regulations, including the Federal Information Security Management Act (FISMA), National Institute of Standards and Technology (NIST) guidelines, and FedRAMP for cloud solutions.
How can agencies detect insider threats?
Insider threats can be detected through behavior monitoring, advanced analytics, and AI-driven tools that identify abnormal user activities and potential security risks.
Why are legacy systems vulnerable?
Legacy systems often lack modern security features like encryption and multi-factor authentication, making them easy targets for cyberattacks.
How can federal agencies modernize their IT infrastructure?
Federal agencies can modernize their IT infrastructure by upgrading legacy systems, adopting FedRAMP-authorized cloud services, and implementing advanced security solutions like encryption and access controls.
What is FISMA, and why is it important?
FISMA is a law that requires federal agencies to implement information security programs to protect sensitive and classified information. It is critical for ensuring compliance and reducing security risks.
What role does human error play in data breaches?
Human error is a leading cause of data breaches, often resulting from mistakes like misaddressed emails, poor password management, or failure to follow security protocols.
Jump to
You May Also Like
These Related Stories
Guide to Audio Redaction Software for Data Privacy & Compliance

Balancing Transparency and Privacy: The Role of Document Redaction


No Comments Yet
Let us know what you think