Control who sees your files and for how long with limited access URLs
Share your redacted files with limited access URLs that become inactive after the defined period. VIDIZMO Redactor offers users ultimate privacy, control, and security for sharing sensitive files via a one time view video link.
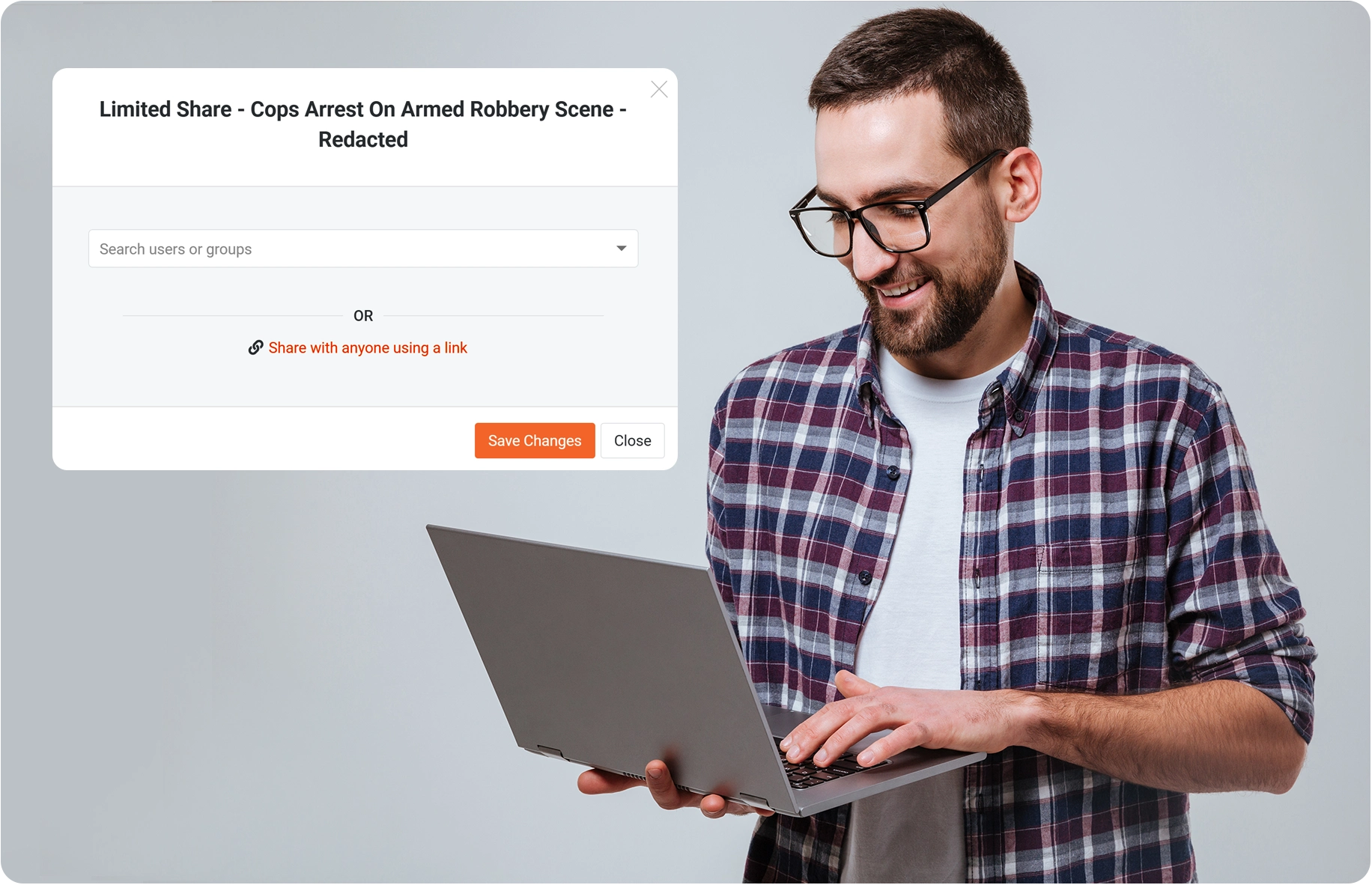
Share files on your terms with limited URLs
Free yourself away from unprotected data-sharing worries with limited access URLs
Securely share specific files with select groups
Share redacted files with specific users or groups by setting viewing or time-bound limits.
Safeguard files by defining limits
Share redacted media with ease through tokenized URLs, allowing you to set time or viewing limits.
Granular access control with limited URLs
Set limitations to ensure redacted files are viewed by only those they are intended for

Set time limits
Share your files using time-sensitive links that stop responding past the specified period. These secure, limited URLs ensure that your redacted files are only viewed or amended by authorized users.

Set view limits
Create multiple links
Users can generate various limited access URLs for a single file. Each link can have different limits and varied permissions. For instance, some users may have the right to amend, whereas others will only have viewing access.
A redaction tool that’s tailored to your needs
Law Enforcement
Solving crimes means dealing with a mountain of evidence. At the end of the day, officers are left with PII scattered across body-worn camera footage, 911 calls, interrogation transcripts, and case images and documents. There's a duty to protect the identities of witnesses, public informants, and victims.
Protect and serve with VIDIZMO Redactor. Redact faces, people, license plates, weapons, and other objects from videos, audio recordings, images, and documents and comply with CJIS, the Criminal Code of 2012, and other strict regulations.
Try now Explore nowLegal
Upholding the law and ensuring justice are big responsibilities, but so are keeping trust and confidentiality in check. Especially when it's one of the only ways legal professionals can uphold the sanctity of the law while avoiding consequences like being disbarred.
Let privileged information in legal documents stay privileged. Stay compliant with the Federal Rules of Civil Procedure and ABA Model Rules of Professional Conduct. Minimize downtime and make the eDiscovery or legal discoprocess a breeze by effortlessly redacting evidence before presenting it to the opposition.
Try now Explore nowHealthcare
Caring for patients is just as important as caring for their sensitive data. Healthcare documents are riddled with personally identifiable information (PII) and protected health information (PHI), making them susceptible to data breaches and potentially resulting in substantial non-compliance penalties.
Protect patient data in healthcare videos, audio recordings, images, and documents with VIDIZMO Redactor. Easily redact sensitive information in various formats, including scanned documents, medical claims, security camera footage, telemedicine consultations, clinical trials, and hospital records. Ensure HIPAA compliance and safeguard PII and PHI.
Try now Explore nowGovernment
Accountability comes at a cost. With limited time to respond to FOIA requests, government agencies are overwhelmed with the burden of redacting information before it reaches the public eye. The sheer number of requests and limited resources make this an ever-increasing challenge.
With AI-assisted workflows, VIDIZMO Redactor simplifies the redaction process for videos, audio recordings, images, and documents. When there is a substantial number of media files, government organizations take advantage of bulk redaction capabilities to effortlessly protect large volumes of sensitive information.
Try now Explore nowCall centers
In call centers, conversations are currency, and exchanging personally identifiable information (PII) is the standard. When customer conservations get recorded, so does the sensitive information within them. Protecting hundreds and thousands of these calls from breaches and identity theft risks isn't easy.
Leverage the power of VIDIZMO Redactor to detect and redact personally identifiable information (PII) such as names, social security numbers (SSNs), addresses, and financial information in millions of call recordings. Say goodbye to manual recording pauses and secure customer information while ensuring PCI DSS compliance.
Try now Explore nowEducation
Knowledge can leave the classroom, but personal information should stay secure on the premises. Educational institutions take on a significant duty to protect the privacy of their students, especially minors.
Protect students' privacy by redacting their personally identifiable information (PII) from images, videos, audio, and documents. Whether it's recorded classes, school records, student IDs, or filled forms, ensure that their faces, spoken PII, and private information are redacted to meet data privacy compliances, such as FERPA and COPPA.
Try now Explore nowFinance
Finance and wealth management has moved from paper to pixel, taking valuable data along for the ride. Account numbers, credit card data, invoices, and policy documents sit in company databases, ready to be preyed upon by malicious threats.
Protect the highly sensitive financial data of clients from tax documents, financial records, bank statements, payment invoices, and other financial documents. Use AI-powered redaction software to comply with PCI DSS and maintain your organization's trust and reputation.
Try now Explore nowTransportation
Steering towards trust and confidentiality doesn't come easy when your passengers aren't merely travelers but carriers of sensitive PII. Whether it's images, documents, audio files, or videos, this data must be kept safe from prying eyes.
Protect PII in cargo documents, booking information, and passenger manifests and ensure compliance with Federal Aviation Administration (FAA) regulations and the International Ship and Port Facility Security (ISPS) code.
Try now Explore nowA redaction tool that’s tailored to your needs
Law enforcement

Solving crimes means dealing with a mountain of evidence. At the end of the day, officers are left with PII scattered across body-worn camera footage, 911 calls, interrogation transcripts, and case images and documents. There's a duty to protect the identities of witnesses, public informants, and victims.
Protect and serve with VIDIZMO Redactor. Redact faces, people, license plates, weapons, and other objects from videos, audio recordings, images, and documents and comply with CJIS, the Criminal Code of 2012, and other strict regulations.
Try now Explore nowLegal

Upholding the law and ensuring justice are big responsibilities, but so are keeping trust and confidentiality in check. Especially when it's one of the only ways legal professionals can uphold the sanctity of the law while avoiding consequences like being disbarred.
Let privileged information in legal documents stay privileged. Stay compliant with the Federal Rules of Civil Procedure and ABA Model Rules of Professional Conduct. Minimize downtime and make the eDiscovery or legal discoprocess a breeze by effortlessly redacting evidence before presenting it to the opposition.
Try now Explore nowHealthcare

Caring for patients is just as important as caring for their sensitive data. Healthcare documents are riddled with personally identifiable information (PII) and protected health information (PHI), making them susceptible to data breaches and potentially resulting in substantial non-compliance penalties.
Protect patient data in healthcare videos, audio recordings, images, and documents with VIDIZMO Redactor. Easily redact sensitive information in various formats, including scanned documents, medical claims, security camera footage, telemedicine consultations, clinical trials, and hospital records. Ensure HIPAA compliance and safeguard PII and PHI.
Try now Explore nowGovernment

Accountability comes at a cost. With limited time to respond to FOIA requests, government agencies are overwhelmed with the burden of redacting information before it reaches the public eye. The sheer number of requests and limited resources make this an ever-increasing challenge.
With AI-assisted workflows, VIDIZMO Redactor simplifies the redaction process for videos, audio recordings, images, and documents. When there is a substantial number of media files, government organizations take advantage of bulk redaction capabilities to effortlessly protect large volumes of sensitive information.
Try now Explore nowCall centers

In call centers, conversations are currency, and exchanging personally identifiable information (PII) is the standard. When customer conservations get recorded, so does the sensitive information within them. Protecting hundreds and thousands of these calls from breaches and identity theft risks isn't easy.
Leverage the power of VIDIZMO Redactor to detect and redact personally identifiable information (PII) such as names, social security numbers (SSNs), addresses, and financial information in millions of call recordings. Say goodbye to manual recording pauses and secure customer information while ensuring PCI DSS compliance.
Try now Explore nowEducation

Knowledge can leave the classroom, but personal information should stay secure on the premises. Educational institutions take on a significant duty to protect the privacy of their students, especially minors.
Protect students' privacy by redacting their personally identifiable information (PII) from images, videos, audio, and documents. Whether it's recorded classes, school records, student IDs, or filled forms, ensure that their faces, spoken PII, and private information are redacted to meet data privacy compliances, such as FERPA and COPPA.
Try now Explore nowFinance
Finance and wealth management has moved from paper to pixel, taking valuable data along for the ride. Account numbers, credit card data, invoices, and policy documents sit in company databases, ready to be preyed upon by malicious threats.
Protect the highly sensitive financial data of clients from tax documents, financial records, bank statements, payment invoices, and other financial documents. Use AI-powered redaction software to comply with PCI DSS and maintain your organization's trust and reputation.
Try now Explore nowTransportation

Steering towards trust and confidentiality doesn't come easy when your passengers aren't merely travelers but carriers of sensitive PII. Whether it's images, documents, audio files, or videos, this data must be kept safe from prying eyes.
Protect PII in cargo documents, booking information, and passenger manifests and ensure compliance with Federal Aviation Administration (FAA) regulations and the International Ship and Port Facility Security (ISPS) code.
Try now Explore nowResources you might be interested in…
All you need to know about PII redaction in transcripts
Read more >People also ask
What is a restricted URL?
A restricted URL means only the group of people or individuals with the specific URL can access confidential information or files.
Why should someone restrict access to files?
Organizations can restrict access to files and data to protect confidential information from unauthorized access. It safeguards files from data breaches, internal and external threats, and other risks.
What is a token URL?
A tokenized URL contains an authentic token that comes with time or usage constraints and is accessible by those it is intended for. Once the time or view limit is reached, the limited access URL expires.